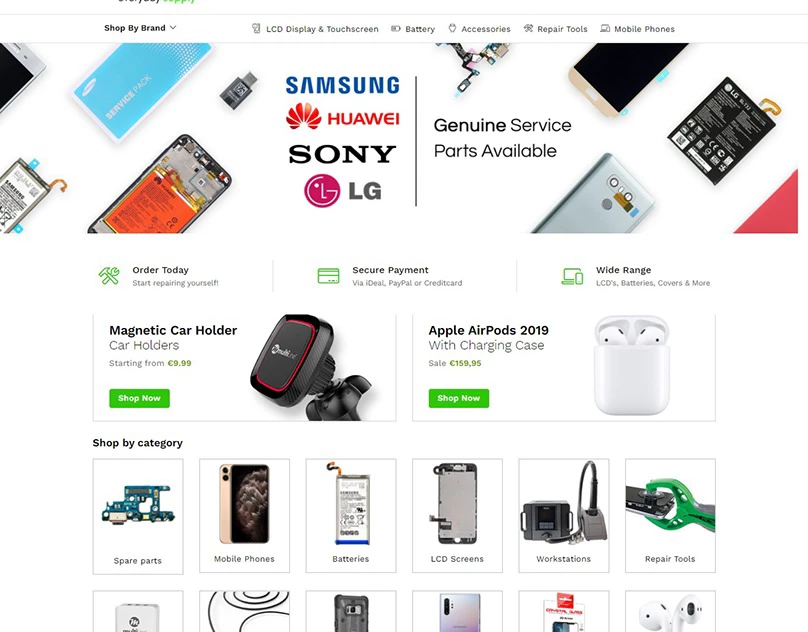
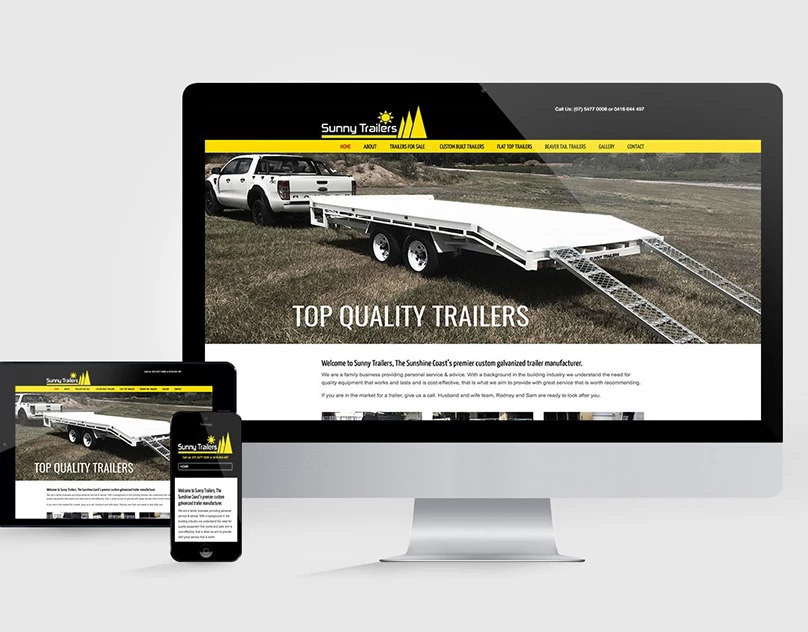
Finding a reliable developer these days can feel like searching...
Read More
Professional Full-Stack Developer | Cloud, DevOps & Security Specialist
Hello, I’m Walid. As a Full-Stack Developer and Cloud, DevOps & Security Specialist, I combine expertise in web development with ethical hacking to build secure, high-performance digital solutions.
What I Offer:
✔ Front-End Development – Responsive and modern UI/UX using HTML, CSS, JavaScript, React, Next.js, and other cutting-edge technologies.
✔ Back-End Development – Robust and scalable server-side solutions with Python, Django, SQL, PostgreSQL, and modern frameworks.
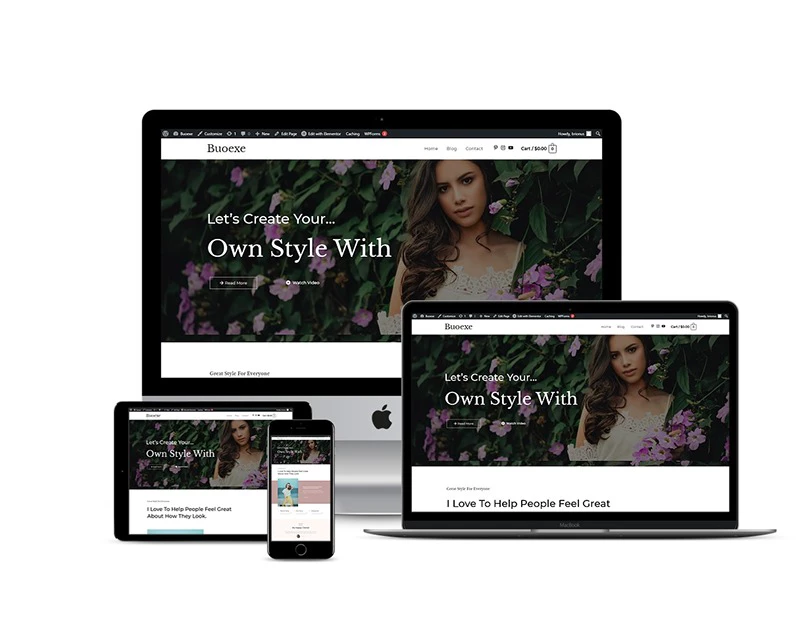
✔ CMS & E-Commerce Solutions – Custom WordPress, Shopify, Wix, and Squarespace development with seamless integrations and performance optimization.
✔ Web Security – Comprehensive vulnerability assessments, penetration testing, and malware protection to ensure your applications remain secure.
✔ Cloud & DevOps – Deployment, automation, and scalability solutions using AWS, Docker, CI/CD pipelines, Kubernetes, and cloud infrastructure management.
Whether you need a fast, responsive website, a secure e-commerce platform, or protection against cyber threats, I deliver tailored solutions for businesses and professionals.
Let’s build something amazing—securely.
What Services I'm Providing
Web Design or Web Development Specialist

Full Stack Web Development with Python, Django / Flask & React
I will develop full-stack web development with Python, Django / Flask & React.

Web application using Python
I will develop a web application using Python, Django, and Flask.

React / Next.js Web development
I will develop a web application using React / Next.js.

Dedicate and VPS Server
- Amazon Web Services.
- Microsoft Azure.
- Google Cloud Platform.
- Cloudways Ltd.
- DigitalOcean Platform.
- Linode, LLC.
- Vultr Platform.
- Alibaba Cloud.

Website Maintenance Services
Ensure your website is regularly updated, stays secure, and out of the reach of hackers with WordPress Website Maintenance Malaysia.

Setup and Management Servers
Efficiently set up and manage your servers with a reliable hosting solution, ensuring high performance and offsite backups available 24/7/365.This keeps the focus on server management and performance while highlighting backup capabilities. Let me know if you’d like further adjustments!

Content management system Website
- WordPress,
- Shopify,
Frequently Asked Questions
Web Design and Web Developemnt
You would need a domain and hosting account. If you don’t have any then don’t worry I’ll assist you. I’ll also need your company logo(optional) & a total number of pages for the website. e.g. Home, About Us, Services, Contact Us, Blog. I’ll further need content (text, images) for these pages.
Yes, The basic structure of your website will be SEO Friendly.
Yes, it’ll be responsive for all devices.
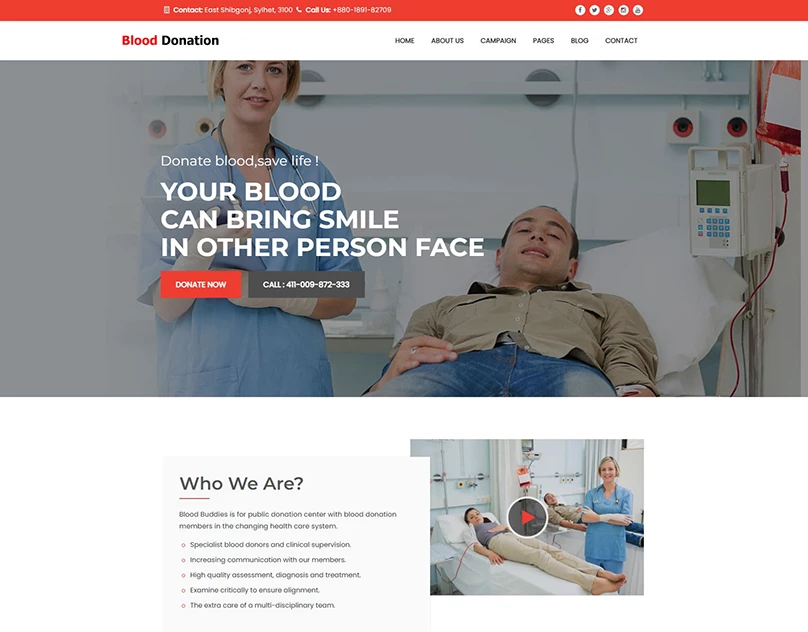
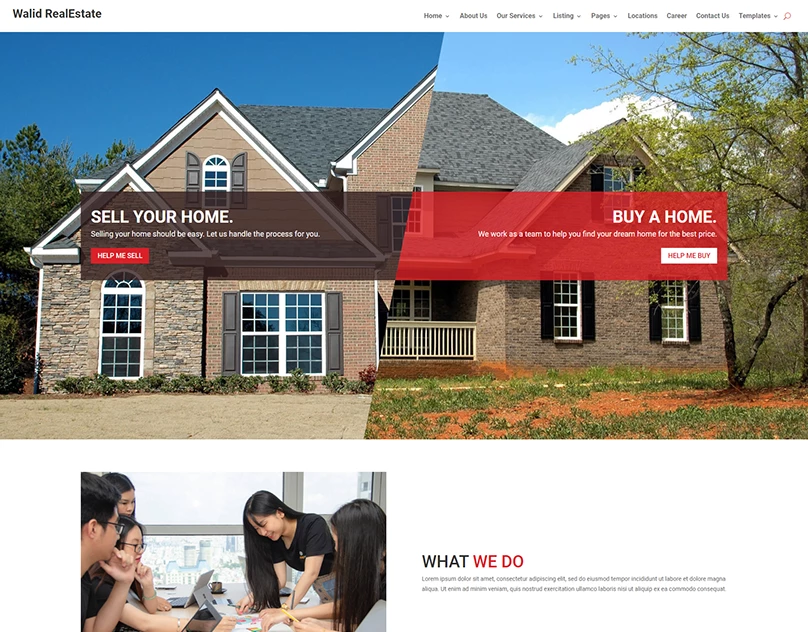
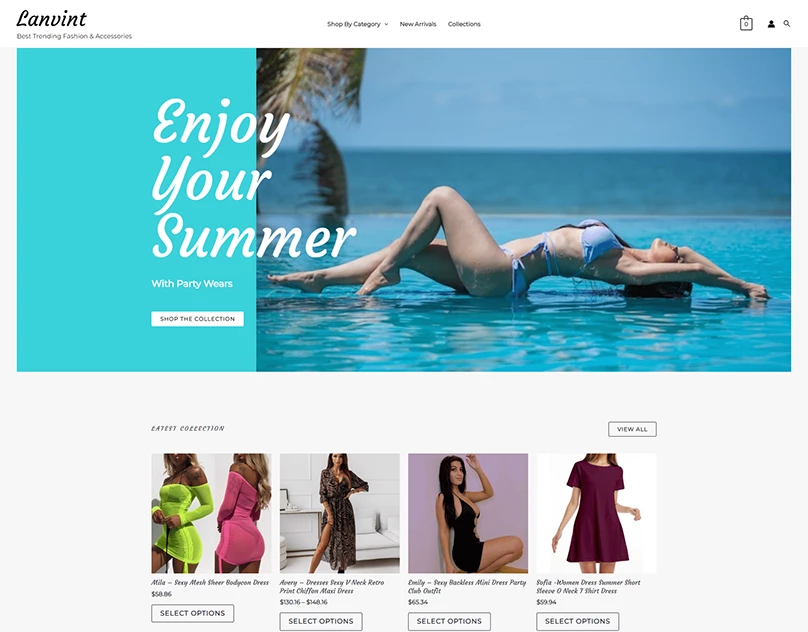
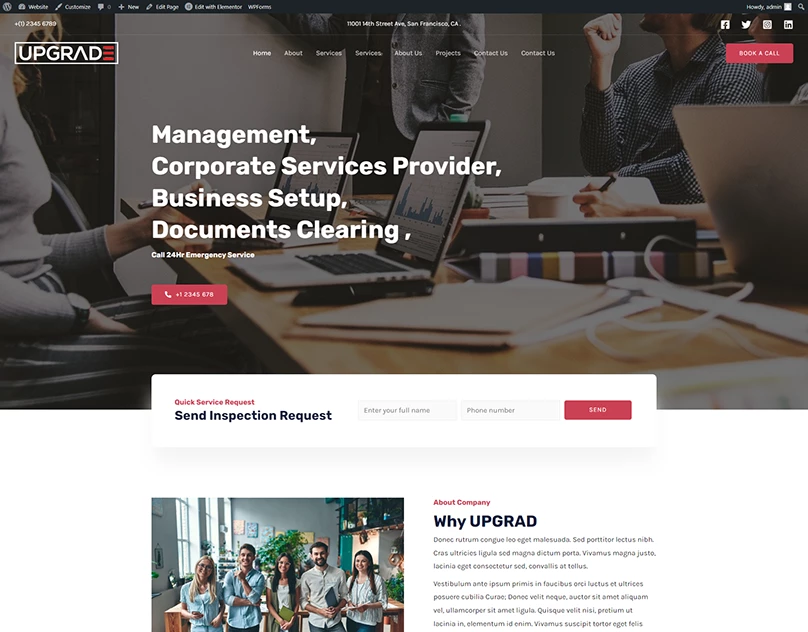
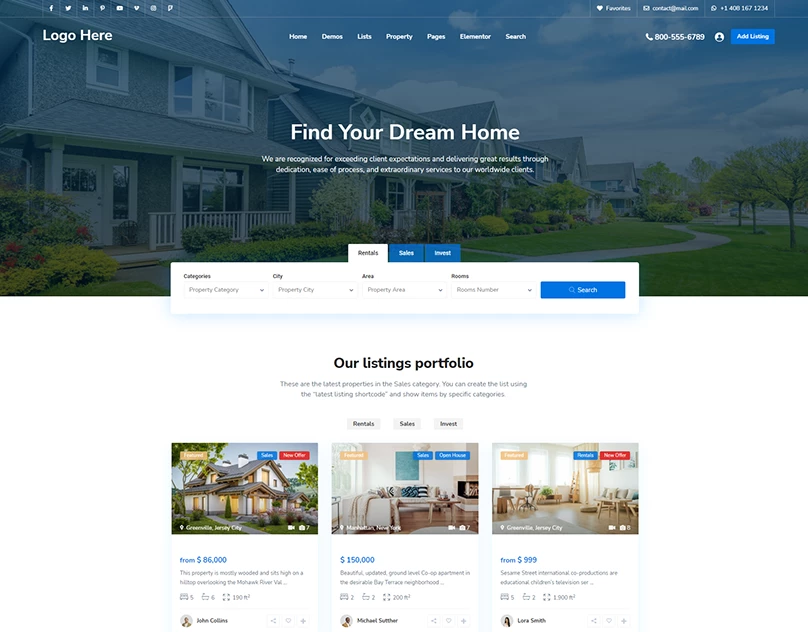
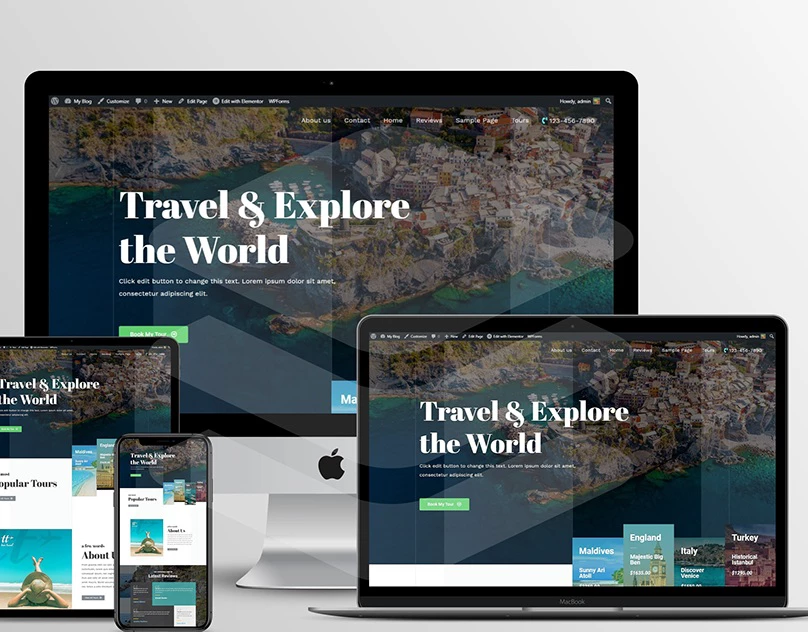
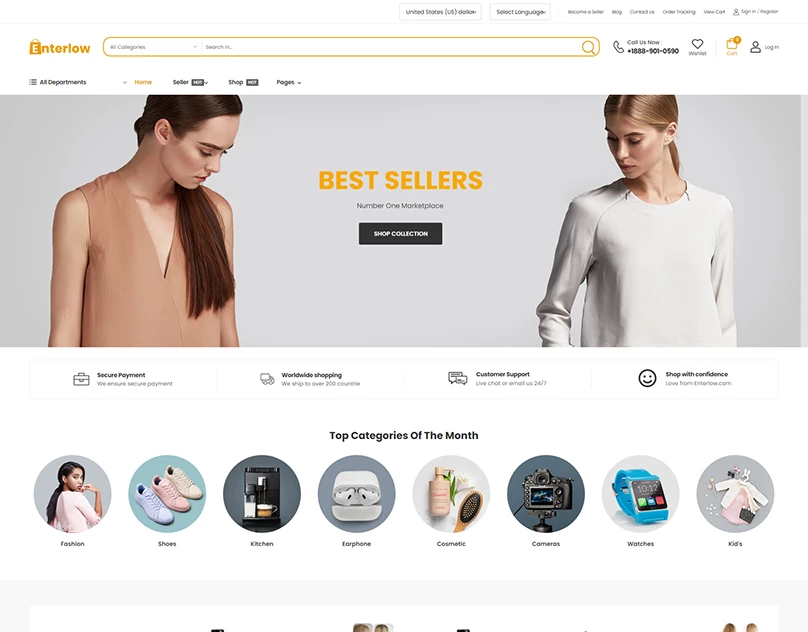
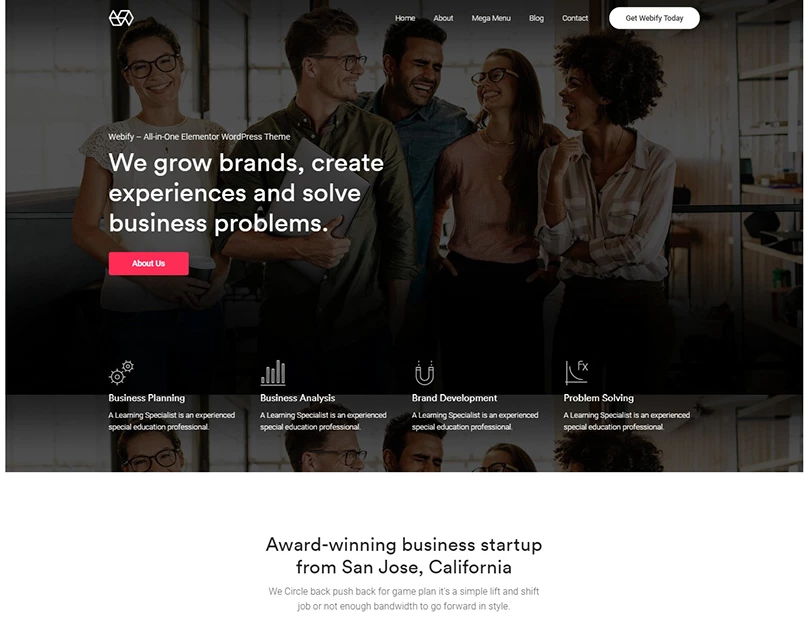
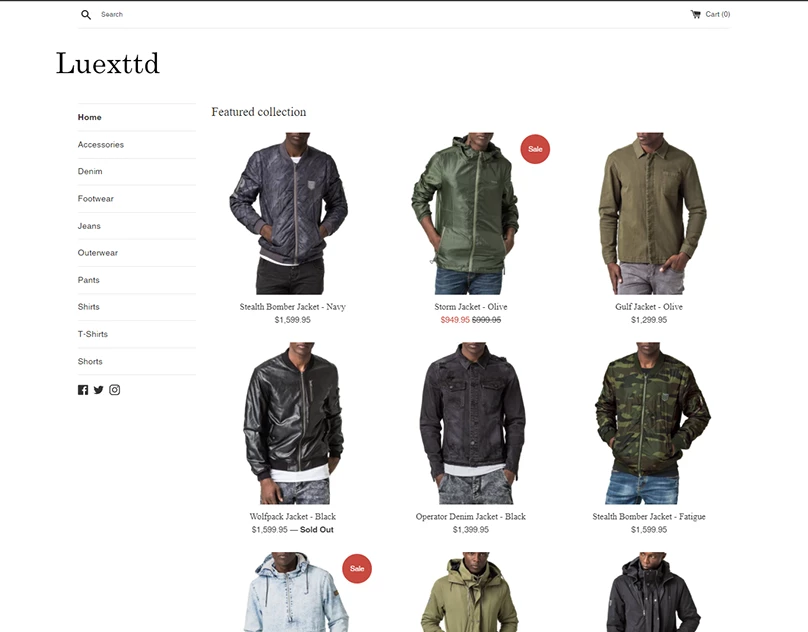
I will design and develop website such as eCommerce, blogs, Corporate websites, Small businesses, Hotel booking and Travel, Medical health and clinics, News portal, Personal Portfolio, Real Estate, Service, News, Student, and CV, Landing Page For Any Product and Business Social, E-Commerce, And More.
I will design and develop website such as eCommerce, Drop shipping Store, Multi-Vendor marketplace.
Nope! We work with clients all over the world.
The timeline for building a WordPress website can vary depending on the complexity of the project. Simple websites can be completed in a few days, while more complex projects may take several weeks. I will provide you with an estimated timeframe after understanding the project scope.
No, But WordPress is a great content management system that has a full spectrum of tools, themes, and plugins that enhance the easy creation of amazing websites. Besides, we also build websites that come with sophisticated functionalities which require custom design & development using PHP language.
What services I'm providing as a
Ethical Hacker or Cyber Security Specialist

Vulnerability Assessment
Recognize vulnerabilities before they may be used against you. Secure critical corporate data, maintain its integrity and confidentiality, and make sure it’s secure before a product is released.

Penetration Testing
Penetration testing finds the faults in your system before a vicious actor does. Network & Web Application Testing, customer- side Security Testing, Social Engineering Testing.
Malware and Other Virus Removal
Website Hacked? or Get any virus I’m here to help you to clean and secure your site. I know how important is your website and will secure it from all the attacks.
Frequently Asked Questions
Ethical Hacker or Cyber Security Specialist
An ethical hacker is a cybersecurity professional who uses hacking techniques and tools to identify vulnerabilities and weaknesses in computer systems and networks, with the goal of improving their security and preventing unauthorized access.
A cyber security specialist is a professional who is responsible for protecting computer systems and networks from unauthorized access, theft, damage or other malicious activities. They develop and implement security measures to safeguard the integrity, confidentiality and availability of data and systems.
A vulnerability assessment is a process of identifying and evaluating weaknesses in a system, network, application, or other IT infrastructure that could potentially be exploited by attackers.
There are several types of vulnerability assessments, including network vulnerability assessments, web application vulnerability assessments, and host-based vulnerability assessments. Each type of assessment focuses on a different aspect of an organization’s IT infrastructure and uses different tools and techniques to identify vulnerabilities.
A vulnerability assessment is a process of identifying and classifying vulnerabilities in a system, whereas a penetration test is an attempt to exploit those vulnerabilities to determine their impact on the system.
Penetration testing, also known as pen testing, is a type of security testing that involves simulating a cyber attack on a computer system, network, or web application to identify vulnerabilities and weaknesses.
Penetration testing is important because it helps organizations identify security weaknesses and vulnerabilities before they can be exploited by attackers. By performing regular pen tests, organizations can improve their security posture and reduce the risk of cyber attacks.
There are several types of penetration testing, including network penetration testing, web application penetration testing, wireless network penetration testing, social engineering testing, and mobile application penetration testing.
Penetration testing is the process of simulating cyberattacks to find and exploit vulnerabilities in a system or network. Its benefits include improving security posture by revealing weaknesses, complying with regulations and standards, reducing the risk of breaches and associated losses, and enhancing trust in the system’s security.
Previous Clients Reviews
Client satisfaction is my first priority






Full stack developer – WalidDeveloper.Com
When you need a website that actually works and keeps...
Read MoreFull Stack Development with Python, Django & React: A Modern Approach
Selecting the correct technology stack is extremely important for modern,...
Read MoreLet's Contact
Could you send me your problem and vision?